How Azure Active Directory and Office 365 Subscription Works?
Here is the Scenario:
“You have a user who is the Global administrator of your Office 365 Tenant. He is able to manage users from the Office 365 portal and there comes a requirement to enable password write back for the users. By password write-back we mean that user should be able to reset their own password at the Cloud and the steps are documented here.
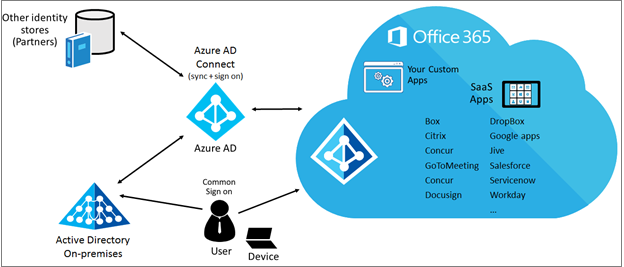
But before following the above, we need to get this “Azure Active Directory” service visible so that we can operate up on it. Password write back is again an Identity management functionality but it’s not manageable anywhere at Office 365 portal but only at Azure AD. So, how to view this “Azure Active Directory” service for your Office 365 tenant? ”
Here is the way: (Frond End – GUI)
- Login to Azure Classic Portal (https://manage.windowsazure.com) and then go to the Active Directory Section.
- Then click on New-> App Services -> Directory -> Custom Create
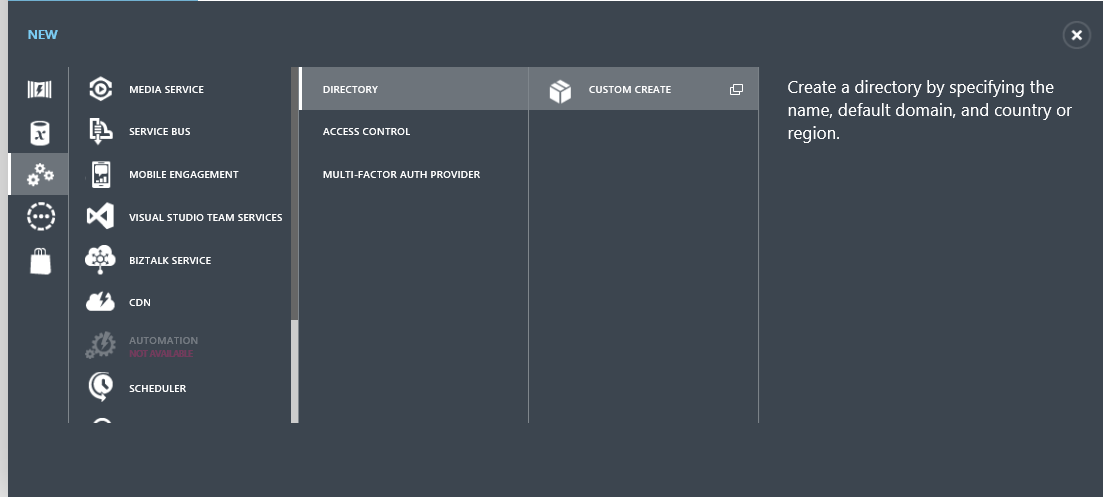
- Click on “Use Existing Directory” (This option comes up for only live accounts who are Service Administrators of the Azure Subscription)
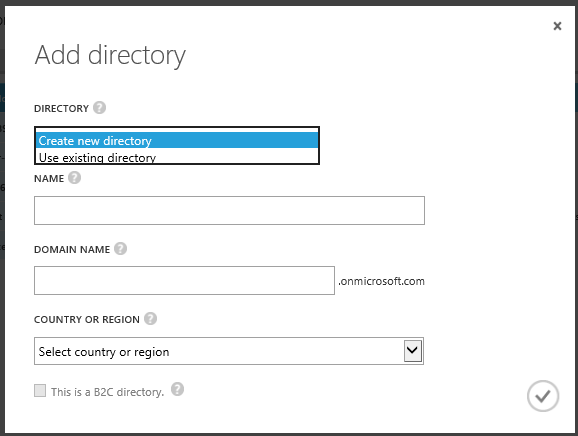
- Click Use existing directory and check I am ready to be signed out now and click the check mark to complete the action.
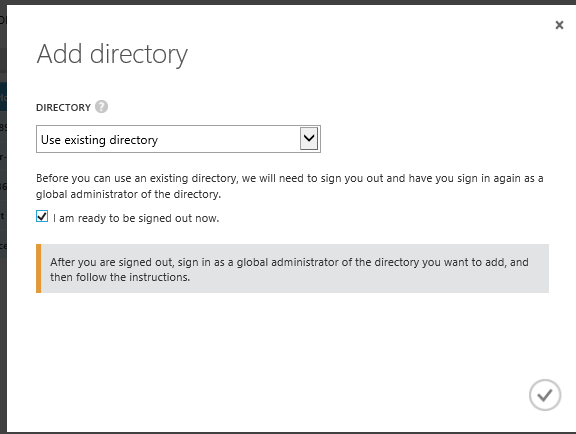
- Sign in to the Management Portal by using and account that is Global Administrator of your Office 365 Tenant.

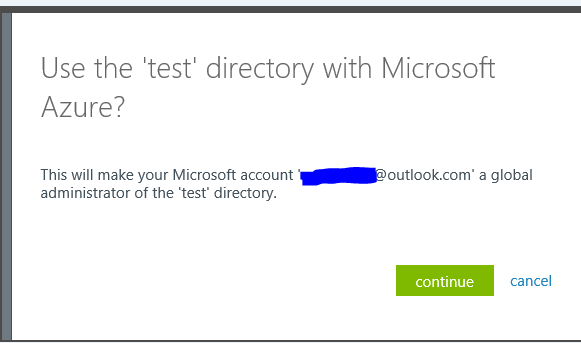
- When prompted to Use the <Tenant-Name> directory with Azure? And click continue.
- Click Continue and Sign out now.
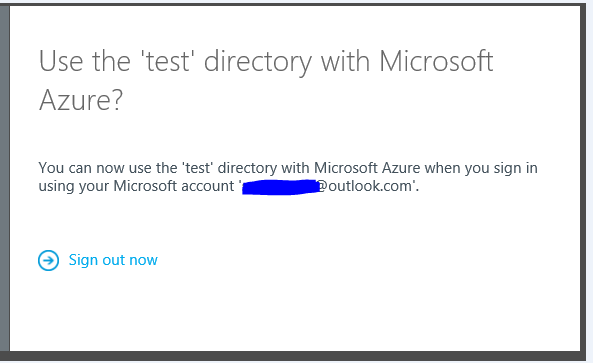
- Sign back in to the Management Portal using your Microsoft account. Your Azure AD Service for the Office 365 SaaS will appear in the Active Directory extension.
![]()
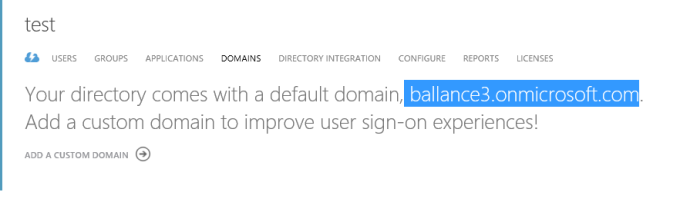
- As we have seen before the key identifier for our Directory is the Tenant Default Domain Name. Our Default domain name was ballance3.onmicrosoft.com and it is reflected here as well:
Now you should be able to click on “Configure” Section and then configure the settings of the Password Write Back or any other available setting for your users.
What Happens in Back-end During the Above Process?
This process seems fairly simple in GUI. But what really happens in the backend? Let’s uncover it. The basic thing that we need to understand here is that if a user needs to manage an Azure AD/Office 365 completely with all the functionalities he needs to be a Global Administrator (which is the same as Office 365 Global Admin) or the reverse: “If the signed in user to the Azure Classic Portal is an Office 365 Global Administrator, he must be able to manage that Identity piece of it – which means the Azure Active Directory – So, he must be able to see the Azure Active Directory Service if he is a Global Admin for it”
So, I actually signed in to Azure portal with my Microsoft Account (which has an Azure Active Directory) which we will take for example as someuser@outlook.com. Now when he follows the above process to add the Azure AD for the Office 365 (Front End), as we have seen already he just chooses to sign-out and signs in with the “Global Administrator” of the Office 365 Tenant after which he gets this below prompt which is significant:

This above prompt gets a consent from the Global Administrator account to add the account “someuser@outlook.com” as a Global administrator user to the directory so that when this user “someuser@outlook.com” signs in the next time, he will be able to see the Directory.
We have followed the above all because the real Global Administrator user of the tenant, in our case – admin@ballance3.onmicrosoft.com does not have a valid Azure Subscription to be able to see its directory in Azure Classic Portal.
What if he has an Azure Subscription somehow? In that case, he will be able to login with that Azure Subscription and manage his directory through Azure Classic Portal itself.